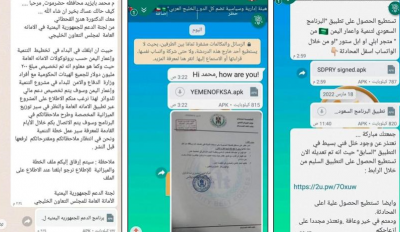
The cybersecurity company "Record Future" has revealed that a hacking group known as "OilAlpha," potentially linked to the Houthi group in Yemen, targeted Yemeni individuals, media outlets, and non-profit humanitarian organizations in the Arabian Peninsula via the "WhatsApp" application as part of a digital espionage campaign. According to a detailed report published by the company, the group’s operations included targeting individuals who participated in consultations sponsored by Saudi Arabia in April 2022. The hackers used deceptive "Android" applications that mimicked entities linked to the Saudi government and an Emirati humanitarian organization.
The hacking group also faked "forged" documents attributed to the Security Belt Forces, affiliated with the Southern Transitional Council in Aden. The company believes that the "OilAlpha" hacking group supports the Houthi agenda. It stated that the group utilized the infrastructure associated with the public telecommunications corporation in Yemen, which is directly controlled by Houthi authorities.
According to the cybersecurity company, "OilAlpha" employed encrypted messaging programs like WhatsApp to launch social engineering attacks against its targets. They also used shortened URL links. Based on assessments of the victims, it appears that most of the targeted entities were Arabic-speaking individuals using Android-operated phones. The hacking group aimed at the devices of some politicians and journalists involved in the Riyadh consultations, using Remote Access Tools (RATs) to install spyware such as SpyNote and SpyMax.
The company believes that the group also impersonated names of Saudi organizations such as the King Khalid Foundation, the King Salman Center for Relief and Humanitarian Action, and the Masam project for landmine clearance. The "Soth24" center, which published the documents, noted that the group impersonated official entities in the Gulf Cooperation Council.
Record Future mentioned that the group also impersonated requests from non-governmental organizations such as the United Nations Children's Emergency Fund (UNICEF) and the Norwegian Refugee Council, as well as the Red Crescent Society. These organizations are either managing or coordinating disaster response and humanitarian work in Yemen.
Record Future pointed out that there is insufficient evidence to determine whether the attackers were Yemeni hackers or other threat groups in the region. It suggested that "external threat actors such as Hezbollah from Lebanon or Iraq, or even Iranian operators supporting the Islamic Revolutionary Guard Corps, may have led this threat activity."